Mobile Code Usually Is Delivered Through ________.
Types of Malicious Code Attacks So what can malicious code do. DSL similarly is delivered via phone lines.
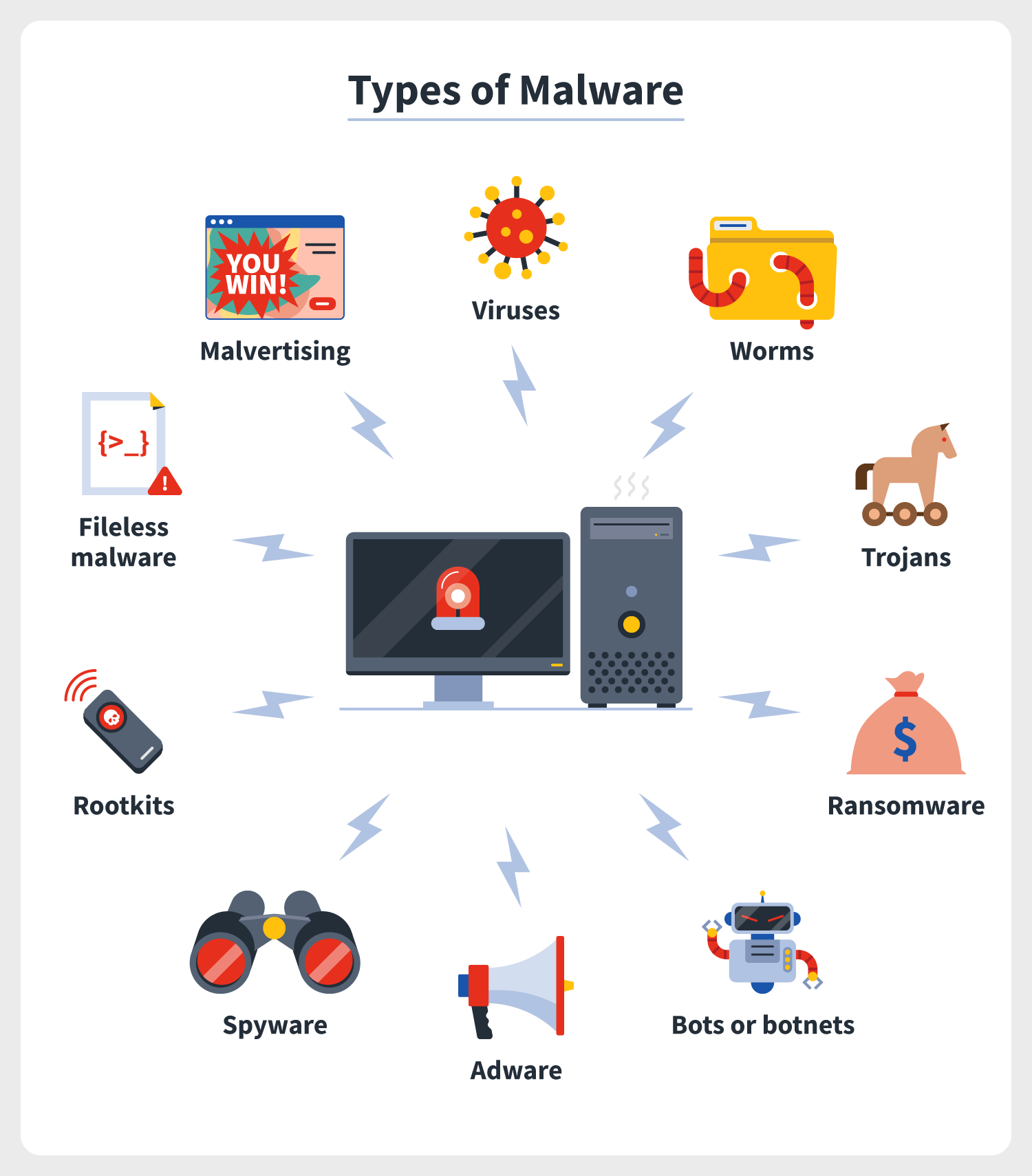
10 Types Of Malware How To Prevent Malware From The Start Norton
Course Title CNT 3406.

. A botmaster can remotely _____. Each day a new variant gets added to the ransomware family. Cable Internet access is usually delivered through TV providers using pre-existing coaxial copper TV cables mounted on telephone poles.
There are a few speed bumps in the path of releasing mobile products even for teams with the most current XPAgileDevOps process. This document contains the transaction summary such as deposits withdrawals charges and balance period. Angularlike most frontend frameworkscomes with some helpful libraries for using validating and processing form data.
Its main method of delivery is through virus-infected email attachments or malicious ads and content running on hacked websites. Mobile code usually is delivered through ________. There are a few speed bumps in the path of releasing mobile products even for teams with the most current XPagileDevOps process.
Mobile apps can work. You receive an e-mail that seems to come from your bank. Mobile code usually is delivered through.
OTPs can also be delivered through proprietary tokens though these are less popular as it requires a person to carry the token at all times. The special characteristics of mobile apps outlined above mean that several parts of your continuous delivery chain need to be designed differently in order to handle mobile. Also when transcribed the messages usually are delivered through email.
However the website is fake. The ransomware threat has significantly grown over time. Most traditional external attackers were heavily motivated by _____.
NIST SP 800-28 Version 2 under Mobile Code NIST Cybersecurity Framework Version 11 under Mobile Code Executable code that is normally transferred from its source to another computer system for execution. However this doesnt mean that the CC server does not send back any data. What is more they are usually delivered through recognizable computer programs such as scripting languages plug-ins ActiveX controls and Java Applets.
C directly propagating worms. Cable 9888 coverage and DSL 9867 coverage. Specifically the following parts of the pipeline require extra attention in order to handle mobile software delivery.
What all of these have in common is their ability to execute themselves once injected into the target system. Speaking of spam emails they are either loaded with malicious document files installing the malware or malware directly inside a ZIP file. Penalties for hacking are _____.
The CC server checks the HMACs validity and returns the 404 Not Found response code if it is invalid. Testing should be a part of any continuous. Sending packets with false IP source addresses is called _____.
The thrill of breaking in. Features like user logins in-app messaging payment processing and custom settings rely on data from the user that is usually delivered through an HTML form. You can expect to find two major infrastructure choices in Baxter coaxial cable 6935 coverage and DSL 9072 coverage.
Coaxial cable Internet service is usually delivered through cable TV providers via coaxial copper television wires strung up on utility poles or buried along the street. DSL similarly is delivered over phone wires. Mobile code uses network or storage media such as a Universal Serial Bus USB flash drive to execute local code execution from another computer system.
Quincy features two major network choices. Malware are usually delivered through exploit kits and spam emails. Mobile code is usually downloaded via the body of an HTML email or email attachment.
A bank statement is a document that will be sent to the account holder each month. To avoid getting your device infested with malware by visiting one of these websites always search for the official domain by typing it into a search engine or by typing it manually into the. If a company wishes to prosecute people or companies that steal its trade secrets it must take.
Up to 375 cash back Maybe theyre sitting in a long presentation maybe theyre on an airplane using a mobile app. D All of the above. This transfer is often through the network eg JavaScript embedded in a web page but may transfer through physical media as well.
School Seminole State College of Florida. Clicking on a link in the message takes you to a website that seems to be your. The term is often used in a malicious context mobile code creates varying degrees of computer and system damage.
Ransomware is a breed of malware that locks your entire device computer tablet smartphone or your files and prevents you from accessing them until you pay a specific amount of money. New software is usually delivered through iTunes or the Google Play store. Mobile code usually is delivered through _____.
Otherwise if the signature is valid the CC server responds with the 204 No Content status code. Pages 15 This preview shows page 6 -. The extent that manual user interaction takes place on mobile is usually in the form of a one-click choice to install an app.
Or as web apps delivered through a browser. Irrelevant of the amount stolen. It simply means that the response body is empty.
Question 14 1 1 pts Mobile code usually is delivered through e mail Correct. All mobile phones can receive SMS there is no requirement for data or an internet connection and the fact that mobile phones usually require their own code to unlock adds even more security. Question 14 1 1 pts mobile code usually is delivered.
Both fix a bug in the bots and update bots with new functionality. Mobile code usually is delivered through _____. New software is usually delivered through iTunes or the Google.
Typically the account holders can review the bank statements each month or even they can view them daily through internet banking. Either way because of voicemail transcription theyre able to stay hands-free or ear-free and not waste time listening. All of the above.
Before getting into the store there are approval and testing procedures that companies must follow.

6 Common Phishing Attacks And How To Protect Against Them
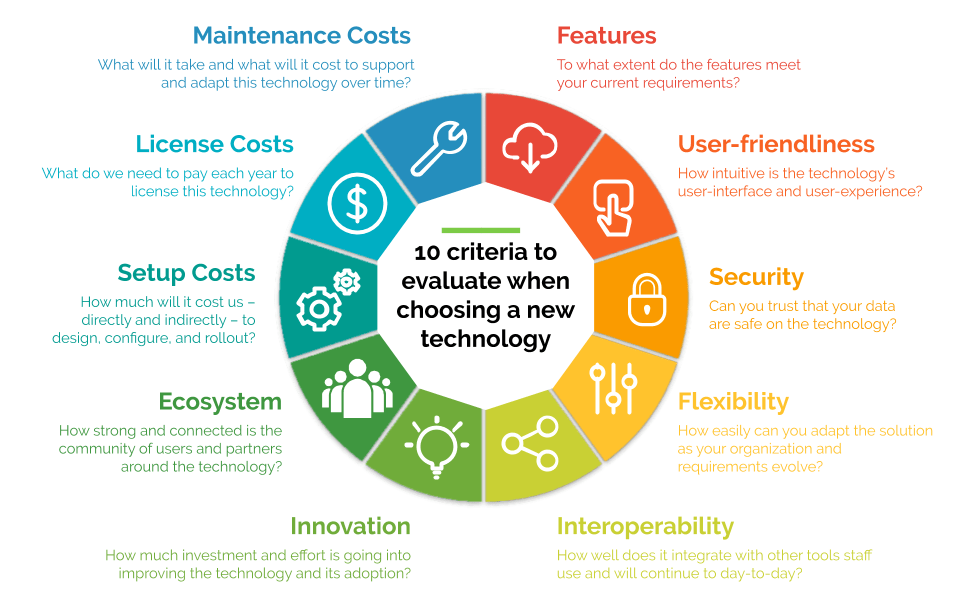
10 Criteria To Evaluate When Choosing A New Technology

What Are Macro Viruses And How Do They Work
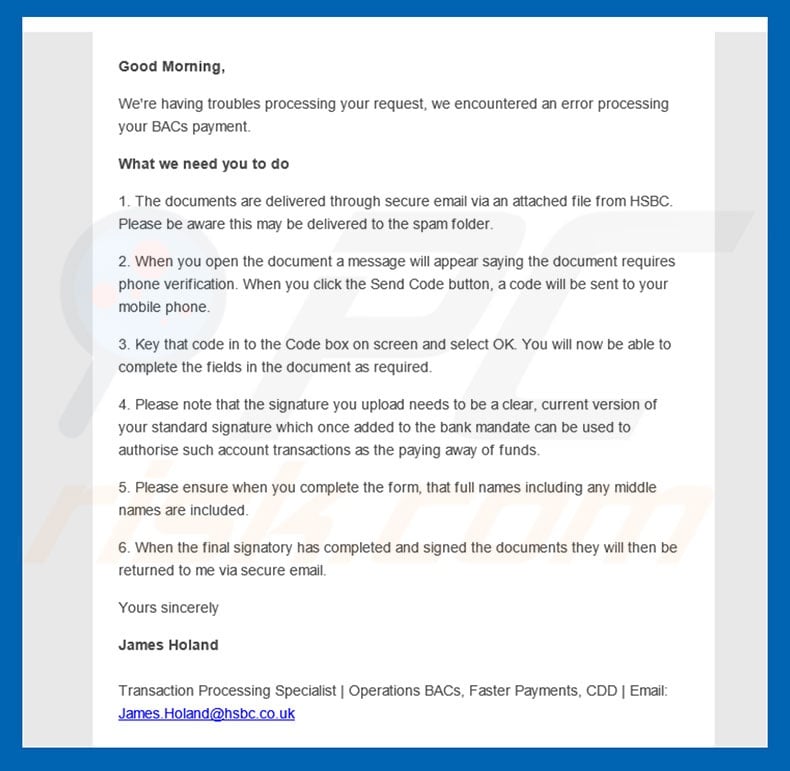
Hsbc Email Virus Removal And Recovery Steps Updated

Mobile Internet Protocol Or Mobile Ip Geeksforgeeks
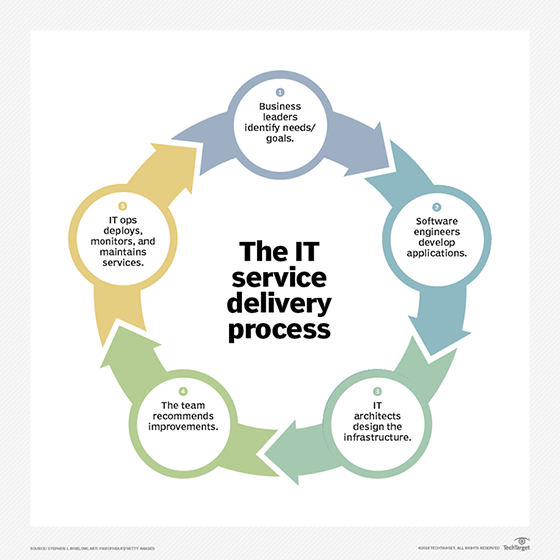
What Is It Service Delivery Definition From Whatis Com

8 Ways To Automate Your Home With Your Phone Infographic Smart Home Technology Smart Home Automation Smart Home
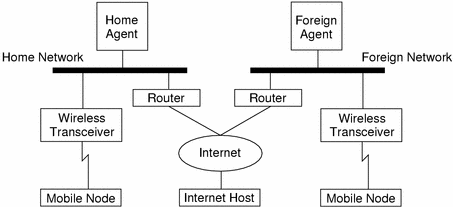
Chapter 1 Overview Of Mobile Ip Mobile Ip Administration Guide
No comments for "Mobile Code Usually Is Delivered Through ________."
Post a Comment